Book your demo
CloudNine has acquired ESI Analyst and are looking forward to working with you.
Click here to request a demo of CloudNine’s ESI Analyst

CloudNine has acquired ESI Analyst and are looking forward to working with you.
Click here to request a demo of CloudNine’s ESI Analyst

Text messages are valuable evidence in litigation and arguing them away is not really an option anymore. Sure, you can try, but smart money is having your client being prepared to produce them through smart preservation and review. Many have often opted for the “screenshot” thinking that is a quick and inexpensive way to preserve relevant text messages. We are here to tell you that you should not believe your own eyes when it comes to these smoking gun screenshots.
Sure, an image of a text message looks real enough, right? And you may be inclined to quickly take it at face value. We are here to tell you buyer beware, as pitfalls lurk around every corner. Let’s break things down. Below is a screenshot of a text message that may be considered relevant to a civil litigation.
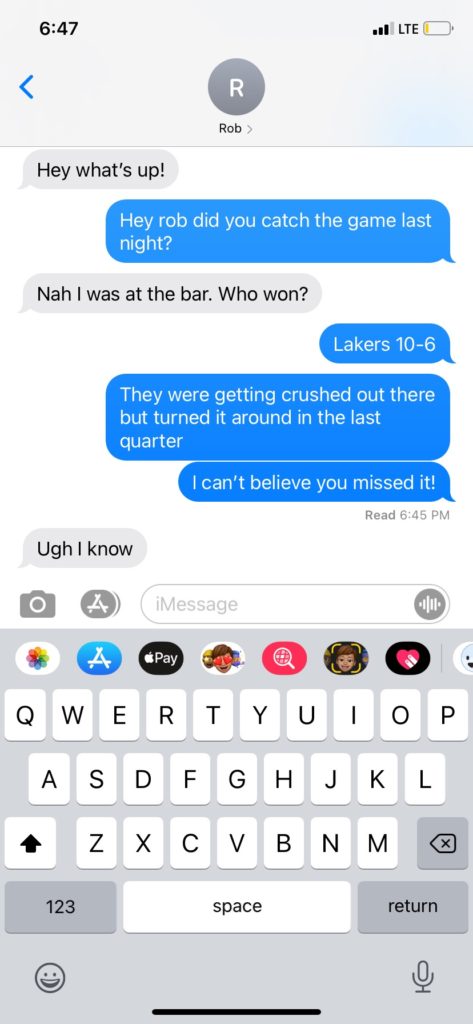
As you can see, we have all of the elements one would expect to see in a text message when displayed on our phone. The phone’s network indicator, battery life, the time on the phone, but what is missing?
First off, while the time on the phone is 6:47 PM that indicates when the screenshot was taken, not the actual date or time this text message exchange occurred. Second, we do not actually know who is participating in this conversation. While we see “Rob” up top, we really do not know who “Rob” really is, do we? And third, this text message exchange never happened. It is not real. It is a fake!
Surprised? You shouldn’t be. It is easy to fake a text message exchange screenshot. After all, it is just an image. Give a good graphic artist 10 minutes in front of Photoshop and bingo, fake text message done. Deep fakes have been taking over the internet in the form of images, video and more for the past few years with stunning believability.
Authentication and proper review of text messages are of the utmost importance to litigation and setting them aside, ignoring them, or failing to properly preserve and establish their authenticity can be a grave mistake. Take the matter of Light (Kipp) v. Esbenshade, 35 Pa. D. & C.5th 58, 72 (C.P. 2013) that occurred in 2013. The Pennsylvania court provided the following opinion.
"Proper authentication of emails and other instant communications, as well as all computerized records, is of critical importance in an ever-increasing number of cases, not only because of the centrality of such data and communications to modern business and society in general, but also due to the ease in which such electronic materials can be created, altered, and manipulated."
Talk about hitting the nail on the head! Lesson to be learned. Don’t believe your eyes.
© 2018 - 2021 ~ TIDAL CHANGE TECHNOLOGIES, INC. ~ ALL RIGHTS RESERVED
CloudNine has acquired ESI Analyst and are looking forward to working with you.
Click here to request a demo of CloudNine’s ESI Analyst